Tools and services for IR and cloud forensics
In this section, we delve into the fundamental aspects of cloud security, focusing on essential tools such as AWS CloudTrail, Azure Monitor, and Google Cloud Logging and Monitoring. These tools are at the forefront of enabling robust security practices within cloud environments. AWS CloudTrail offers comprehensive auditing capabilities, Azure Monitor provides insights into performance and application health, and Google Cloud Logging and Monitoring ensures visibility and control across services. Let’s unravel the capabilities of each, understanding how they contribute to effective security, monitoring, and IR in the dynamic landscape of cloud computing.
AWS CloudTrail
AWS CloudTrail provides detailed logs of API activity across AWS services, enabling organizations to monitor and investigate security incidents in the cloud.
AWS CloudTrail is a service provided by AWS that enables organizations to monitor and log all activity within their AWS accounts. It provides detailed event history for actions taken by users, services, or applications, allowing users to gain insights into who did what and when in their AWS environment. CloudTrail helps enhance security, compliance, and operational auditing by providing an audit trail of actions taken in the AWS Management Console, the AWS Command Line Interface (CLI), and AWS SDKs.
Figure 7.1 depicts the interaction and placement of CloudTrail with various other AWS services’ system managers and end users:
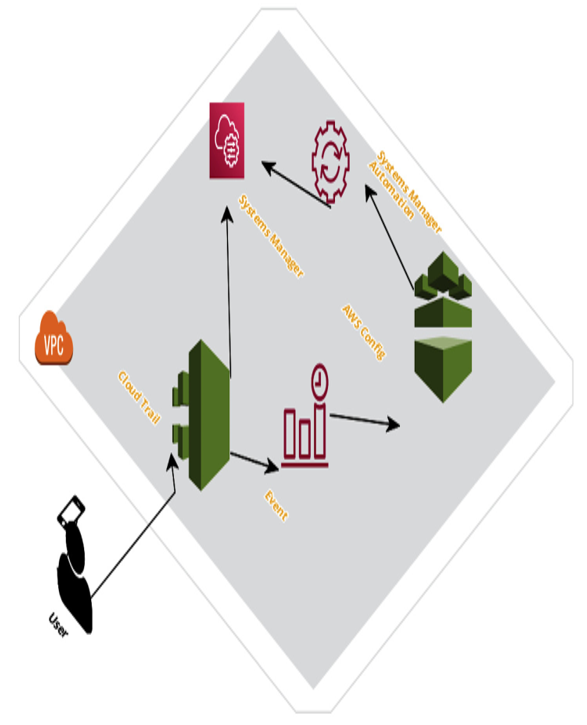
Figure 7.1 – CloudTrail in AWS
In the preceding diagram, we can see how the user connects with the CloudTrail service, which records every API call made through the user within an AWS cloud account, and how the CloudTrail service integrates with the CloudWatch service.
Key features of AWS CloudTrail include the following:
- Detailed logging: CloudTrail captures and records every API call made within an AWS account, including the identity of the entity making the call, the time of the call, the source IP address, and other relevant details.
- Multi-region support: CloudTrail can be enabled in multiple AWS regions, ensuring that all activity across different regions is centrally logged and monitored.
- Integration with CloudWatch: CloudTrail can be configured to deliver its log data to Amazon CloudWatch Logs. This enables users to set up alarms and notifications based on specific API activity, helping them to detect and respond to potential security threats in real time.
- Encryption and data integrity: CloudTrail logs are encrypted to ensure data confidentiality. Additionally, the integrity of the logs is maintained by using digital signatures to detect any unauthorized changes.
- Log file integrity validation: AWS CloudTrail provides log file integrity validation, enabling users to verify the authenticity of log files and ensure they have not been tampered with.
- Simple Storage Service (S3) bucket integration: CloudTrail logs can be stored in an S3 bucket of the user’s choice, providing flexibility and scalability for log storage.
- Integration with AWS Config: CloudTrail can be integrated with AWS Config to provide a more comprehensive view of AWS resource changes and configurations.